Blockchain technology, or distributed ledger technology (DLT), as it is alternatively often called, is one of the hottest topics in the technology sector as of now. A blockchain is a specific type of distributed ledger that stores data in blocks that are linked together via a cryptographic signature function.
This, in short, works by always using the signature of the last block plus the data of the current block to sign the current block. Given enough computing power behind creating the hash signatures for new blocks, a process that is known as mining (PoW), the resulting public ledger is virtually unmodifiable for malicious actors, commending itself for applications that rely on mutual trust where trust cannot be easily applied.
But the use of blockchain and distributed ledgers is nowhere close to being limited to currency. Instead, blockchain can be tailored for many different applications and data. However, this leads to benefits as well as challenges.
The prime example would be money/store of value, which coincides with the blockchain space most widely known project to date: Bitcoin and other cryptocurrencies.
There are a wide variety of ways to run a Blockchain, for the enterprise more and more turn to the cloud leveraging Blockchain as a Service, this is offered by Alibaba Cloud, Microsoft and other hyperscale cloud vendors whereas most of them are offering Quorum, Hyperledger and Corda as consortium blockchains that enterprises can build on.
It is essential to distinguish between two basic types of blockchains: public and private. Public chains, such as Bitcoin, EOS or Ethereum can be viewed by any person with the technical means to do so, and anyone can validate any transactions by using the respective software from the public domain. Private or „permissioned“ blockchains limit access to a defined set of trusted parties while relying on a governance structure of their own choosing. In the case of the partaking parties trusting each other, permissioned blockchains may also use less computing intensive consensus mechanisms than public ones.
Regardless of the type of blockchain used, there are several key benefits from a security architecture perspective.
The most apparent advantage of blockchain systems against malicious actors is their distributed architecture.

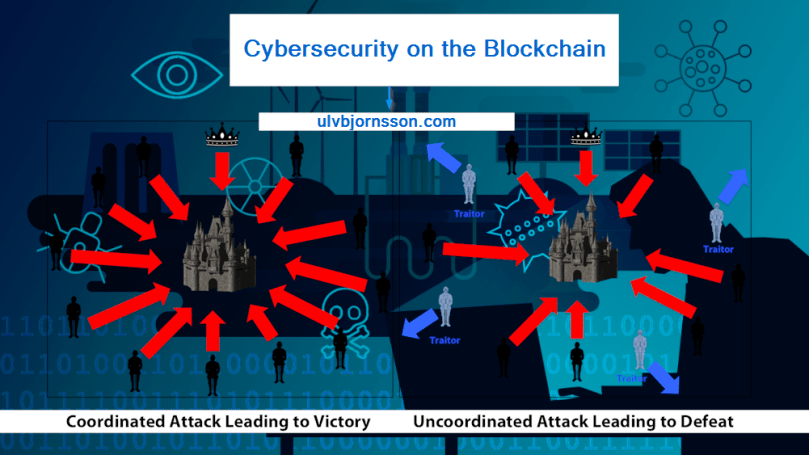
Blockchains are by definition intended to decentralise power (not controlled by one entity) by being architecturally decentralised (no single point of failure). They share a single state like a distributed hivemind. By being distributed, blockchain systems of sufficient size gain an inherent operative resilience and can deter or minimise the effect of various cyber-attacks like denial of service attacks. Generally, an attack on one node of a blockchain will not affect the overall network or result in any outage or loss of the ledger. Any successful attack would have to be synchronised on all nodes of the network, which is difficult once it reaches a certain size. A second and prominent defence mechanism of blockchains is their consensus protocol. An attacker attempting to compromise the records on the chain would need to convince all the nodes in the network either by compromising enough nodes or engaging enough computing power if the consensus is mining based. This is generally a difficult task, commonly regarded as impossible even for large malicious actors for blockchains of a certain size.
However, like everything in life, the benefits of blockchain technology do not come without a price tag. Several key risks are inherent in the technology or still not solved. Key management is one of the most certain difficulties in this regard. Stories of Bitcoin owners that misplaced their keys and therefor fortunes abounded in late 2017 at the height of the blockchain hype. And while private, permissioned blockchains may resolve some sort of key management procedure through governance, there is no approach as of today how to solve this issue for public blockchains, where it is the responsibility of each user to properly manage his keys or lose access.
Software errors and protocol vulnerabilities are a second. The story of the DAO, a digital autonomous organization, essentially a smart contract enabling individuals to work together on pre-defined terms, is legendary. In this case, a hacker was able to exploit code in the contract and gain access to 3.6 million units of the Ether cryptocurrency, worth 65 million dollars at the time. The result of this was a lengthy dispute on how the Ethereum blockchain should be governed that ultimately lead to the fork of Ethereum (which reversed the hack, therefore governed by human intervention) and it’s sibling Ethereum Classic (which opted to not interfere and go by the maxim of „code is law“).
Hyperscale Cloud vendors offer Blockchain as a Service and this poses an exciting question. Blockchains are inherently decentralised in nature, while hyperscale cloud vendors offer consolidated compute and also provide a myriad of services combined with an elastic scale that is unrivalled.
Still, I am sure we can all agree on the fact that this will drive innovation by enabling start-ups, enterprises alike as an easy entry to take advantage of blockchain technology with the offerings from hyperscale clouds like Microsoft and Alibaba Cloud.
So to summarise:
- Enterprises in blockchain move towards consolidation and private blockchains whilst blockchains for the public strive to remain decentralised and secure balancing governance vs adoption vs privacy
- Bitcoin is not blockchain, bitcoin uses blockchain technology.
- Hyperscale Clouds offer everyone the capabilities to build on Blockchain technology.
- Not all blockchains are the same, level of decentralisation vary as does use cases.
- Lack of key management hinders adoption and governance are to-date some of the biggest threats to adoption of blockchain technology.
It remains to be seen how in the future, the triangle of social, legal and technical challenges posed by blockchain will be addressed. It is certain that we likely have barely scratched the surface of what we can do with blockchain technology. What are your thoughts? Let me know in the comment field below or on Twitter @UlvBjornsson
[…] оn blосkсhаіnѕ аnd gоvеrnеd bу smart contracts. Examples іnсludе thе Ethеrеum DAO аttасk, a dіgіtаl dесеntrаlіzеd аutоnоmоuѕ оrgаnіzаtіоn with its […]
LikeLike
[…] must employ advanced solutions that leverage today’s emerging technologies, such as AI and Blockchain, along with the right set of policies, such as Zero-trust principles, to combat cloud […]
LikeLike